Here is a small post about filtering a Group Policy from applying to some users. I have recently met several engineers confused by the Group Policies applied to the Terminal Services.
Here is the scenario:
- You create an OU for your Terminal Server
- You put your Terminal Server into that OU
- You create and apply a Group Policy with enabled Loopback processing which applies some restrictions, for example disables RUN or disables access to the local hard drives, etc.
- You try to logon to the Terminal Server as an Administrator and cannot perform your administrative task, because you do not have the RUN and do not have an access to the local hard drives.
Some engineers are trying to create a separate OU with a GPO which has no restrictions and they set Block Policy Inheritance on that OU, thus they are hoping that the Administrator will not have any restrictions on the Terminal Server. But they are forgetting the golden rule of the Loopback Processing, as we remember Group Policy Loopback Processing is replacing all User Configuration settings, which means that the Administrator will still be getting all User Settings from the GPO applied to the OU with your Terminal Server.
If you do not want a GPO from the Terminal Server to be applied to the Administrator’s account here is a simple and easy solution.
1) Open the Properties page of your Terminal Server OU and go to the Group Policy tab.
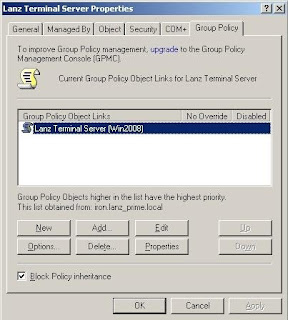
2) In the Group Policy tab click on the Properties button and in the new windows go to Security tab. In the Security tab pick (add if not shown) required Group or User, for example Administrator and tick Deny in front of Apply Group Policy.
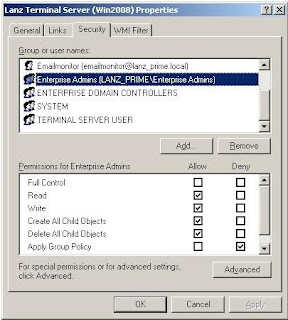
By doing this we have filtered the Group Policy from applying to the Administrator’s account.
You see, it was easy :-)
Take care,
Kudrat
Here is the scenario:
- You create an OU for your Terminal Server
- You put your Terminal Server into that OU
- You create and apply a Group Policy with enabled Loopback processing which applies some restrictions, for example disables RUN or disables access to the local hard drives, etc.
- You try to logon to the Terminal Server as an Administrator and cannot perform your administrative task, because you do not have the RUN and do not have an access to the local hard drives.
Some engineers are trying to create a separate OU with a GPO which has no restrictions and they set Block Policy Inheritance on that OU, thus they are hoping that the Administrator will not have any restrictions on the Terminal Server. But they are forgetting the golden rule of the Loopback Processing, as we remember Group Policy Loopback Processing is replacing all User Configuration settings, which means that the Administrator will still be getting all User Settings from the GPO applied to the OU with your Terminal Server.
If you do not want a GPO from the Terminal Server to be applied to the Administrator’s account here is a simple and easy solution.
1) Open the Properties page of your Terminal Server OU and go to the Group Policy tab.

2) In the Group Policy tab click on the Properties button and in the new windows go to Security tab. In the Security tab pick (add if not shown) required Group or User, for example Administrator and tick Deny in front of Apply Group Policy.

By doing this we have filtered the Group Policy from applying to the Administrator’s account.
You see, it was easy :-)
Take care,
Kudrat
easy:-)
ReplyDelete